If you are actively involved in cryptocurrency, you should be conservative and protect your digital assets using various cryptocurrency wallets. A cryptocurrency wallet is essentially a software program that stores cryptographic keys and interacts with blockchains for users sending and receiving cryptocurrencies as well as checking their balances. Unlike a traditional wallet in your pocket, a cryptocurrency wallet doesn’t store currency, but instead stores all the private keys associated with the generated wallet addresses. Those private keys are utilized to unlock the funds in your wallet and sign off the ownership of cryptocurrencies. Cryptocurrency wallets can be classified into two categories, namely hot wallets and cold wallets. While hot wallets are meant to be used on a daily basis and typically connected to the Internet to quickly access the blockchain, cold wallets are mainly kept offline for less exposure and utilized for long-term storage of cryptocurrencies. In practice, hot wallets can be implemented as desktop, online or mobile applications, whereas cold wallets include paper and hardware wallets. This blog post focuses on hardware wallets, one of the most secure types of cryptocurrency wallets.

Source: https://cryptoshortlist.blogspot.com/2017/10/what-are-different-types-of.html
Cryptocurrency Hardware Wallets
A hardware wallet, which is also a cold wallet, is a dedicated piece of hardware that provides enhanced security features for storing private keys in the long-term and signing transactions offline. Typically, hardware wallets are connected to a computer via a USB port or to a mobile device via Bluetooth or NFC for checking the blockchain. Moreover, hardware wallets are able to work with various web interfaces and support multiple cryptocurrencies. In particular, the private keys are stored in the protected area of a hardware wallet and never been transferred out of the device in plaintext. Hardware wallets achieve a good balance between facilitating the blockchain transactions and keeping your digital assets offline and away from danger.
Security Risks for Hardware Wallets
While hardware wallets offer increased security and trust for the data processed and stored in the device, they also need to be protected from a wide variety of attacks, including but not limited to:
- Remote Attacks: The attacker might steal your private keys or swap recipient addresses of cryptocurrencies through malware on your PC or mobile devices.
- Weak Random Number Generators: Hardware wallets generally rely on onboard physical random number generators to generate private keys for your wallets. The attacker might find the vulnerabilities for the random number generation process and predict your private keys.
- System Bugs: The attacker might take advantage of system bugs at the software, firmware and hardware levels to gain unauthorized access to the secret information stored in hardware wallets.
- Supply Chain Attacks: The attacker might modify hardware wallets (e.g., insert the malicious codes into the firmware, replace the hardware components, etc.) before shipping them to customers.
- Side-Channel Attacks: The attacker might obtain physical access to your hardware wallets and conduct various side-channel attacks (e.g., timing, power, fault, etc.) to extract your private keys and compromise the device.
Properties for Highly Secure Hardware Wallets
Designing a highly secure hardware wallet is a challenging task. By considering various attacks against hardware wallets and analyzing the security designs of popular hardware wallets in the market such as Ledger Nano S, Trezor, KeepKey, etc., we summarize the following properties which we think a highly secure hardware wallet should have:
Ledger Nano S, Trezor, KeepKey
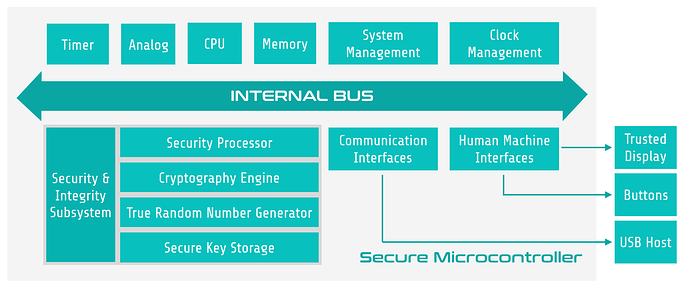
- Hardware-Based Root of Trust: A hardware wallet should have a hardware-based root of trust (e.g., secure microcontroller, secure element, hardware security module, etc.) to securely store private keys and process transactions. These security components are dedicatedly designed to protect sensitive information against a wide range of physical attacks.
- Layered Security and Defense in Depth: Multiple security countermeasures should be in place to address a wide range of potential attacks in the case that the attacker steals your hardware wallet, reflashes the device with malicious firmware, or compromises your PC or mobile devices.
- Transaction Display and Confirmation: A hardware wallet should be equipped with a trusted display for verifying the transaction information as well as on-device buttons for confirming or denying transactions.
- Compartmentalization for Cryptocurrencies: For hardware wallets supporting multiple cryptocurrencies, each cryptocurrency application should run in its own compartment that is protected by hardware-enforced boundaries, which effectively isolates different applications and prevents a flaw found in one application from affecting the rest of the system.
- Certificate-Based Authentication: Digital certificates should be used in the system for hardware wallets securely updating their firmware and enabling device manufacturers to conduct remote attestation.
A high-level system architecture of a secure hardware wallet satisfying the above properties is illustrated below:
Figure. System Architecture of a Secure Hardware Wallet
Next-Generation TrustZone-Based Secure Hardware Wallet — An Outlook
A Trusted Execution Environment (TEE) is an environment that allows for the secure execution of applications. TEE aims to achieve the following five security properties:
- Isolated Execution: TEE should allow applications to be run in an isolated manner, which ensures that malicious applications are not able to access or modify the code and data of other applications.
- Secure Storage: TEE should provide secure storage for protecting the secrecy and integrity of sensitive application data as well as application binaries.
- Remote Attestation: TEE should allow parties to communicate with the secure execution environment to check the authenticity of the software and/or hardware that implements the TEE.
- Secure Provisioning: TEE should ensure the data secrecy and integrity when sending the data to a specific software module operating in the execution environment of a specific device.
- Trusted Path: TEE should be able to communicate with the outside world while ensuring the authenticity and optionally secrecy and availability of the communicated data.
It is not difficult to find similarities between the security properties required by highly secure hardware wallets and those offered by TEE. As a result, TEE provides an ideal solution for further enhancing the security of hardware wallets. While there are several methods to realize TEE, ARM TrustZone is thought to be the most promising technology to implement TEE in ARM-based mobile devices and embedded platforms.
ARM TrustZone is a system-wide security approach for the ARM Cortex-based processors. Unlike the dedicated cryptographic engines with pre-defined functionalities, ARM TrustZone represents a more flexible security solution by leveraging the CPU as a programmable trusted environment. It also offers protection when data is being processed in lieu of just providing cryptographic functions. The basic concept of TrustZone is to have a single physical processor core running the two virtual worlds, namely Secure World and Normal World, in a time-slice fashion. While the Secure World is responsible for accessing sensitive hardware, processing critical data and executing trusted software, the Normal World is the common execution environment for operating systems and other applications. These two virtual worlds are achieved by separating both software and hardware resources. Moreover, the TrustZone technology employs multiple hardware features to facilitate the switching between two virtual worlds. For more details for the ARM TrustZone, the interested reader is referred to Layered Security for Your Next SoC – Arm®.
Source: Upcoming ARM TrustZone Webinars Explaining Embedded Systems / IoT Security to Non-security Experts - CNX Software
A hardware wallet implementation is generally composed of three main groups of functions: wallet storage functions, wallet management functions, and cryptographic operation functions. For realizing a hardware wallet using the ARM TrustZone technology, all the functions, and their associated data need to be fully analyzed in order to determine the functions that should be executed in the Secure World and Normal World, respectively. For example, the functions for handling cryptographic keys should only be executed inside the Secure World. Moreover, the switching between two virtual worlds must be carefully investigated to ensure no sensitive information is leaked during this process. IoTeX is actively conducting research in this area to further enhance the security of hardware clients of blockchains