The Internet of Trusted Things
A machine-driven, automated, and connected future is coming. The spectrum of how the Internet of Things (IoT) is being integrated into our lives is very diverse — fully autonomous vehicles, collaborative robots (“cobots”) that aid workers, AI chips embedded into humans, and more. The question is no longer if but when the IoT will transform society. But a more important question is: can we fully trust the rapidly evolving Internet of Things?
Guaranteeing trust will not come from terms & conditions or regulations. Rather, new technologies that prioritize trust and privacy by design will drive a safe transition into this next technological revolution. This is where IoTeX comes in — by combining blockchain, secure hardware, and data services innovations, IoTeX is empowering the Internet of Trusted Things and enabling **end-to-end trust **.
In this post, we explain what end-to-end trust really means / why it matters, as well as the massive future impact of the **Internet of Trusted Things **.
The Internet of Trusted Things
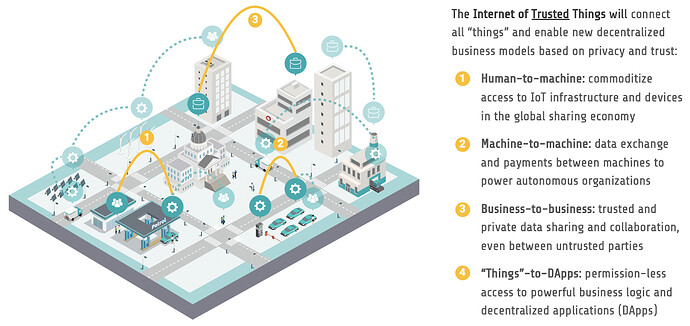
The Internet of Trusted Things, where all physical and virtual “things” — humans, machines, businesses, DApps — can securely exchange data and value at a global scale.
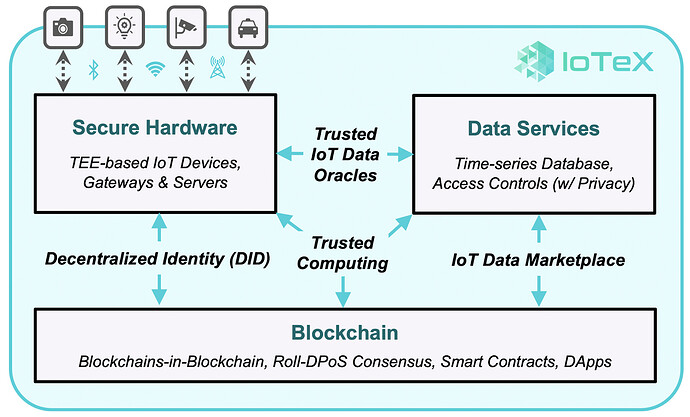
IoTeX’s vision is much more than just adding trust to IoT devices. Rather, IoTeX will serve as the decentralized trust fabric to connect and embed trust in all “things”. In the Internet of Trusted Things, humans, machines, and businesses are all assigned a standardized decentralized identity (DID), allowing them to interact in a peer-to-peer (P2P) fashion. By replacing semi-trusted middlemen with fully trusted code, IoTeX will unlock transformational business models rooted in trust, privacy, and decentralization:
- Humans transact directly with machines in the sharing economy and data/device-as-a-service use cases
- Machines exchange data and payments with other machines to power decentralized autonomous organizations (DAO)
- Businesses and other businesses, including partners and even competitors, collaborate in data sharing and collective intelligence
- And more combinations to form trusted multi-party workflows
The Internet of Trusted Things will change the world; however, a holistic platform like **IoTeX is needed to turn this vision into reality **. From day one, IoTeX’s industry-leading team has made upfront design decisions to fulfill our vision (e.g., secure IoT hardware, interoperability, privacy by design). After two years of rigorous development, IoTeX is excited to announce the genesis of the Internet of Trusted Things is finally here!
Before the full-scale Internet of Trusted Things, there must first be trusted things — IoTeX is launching the first secure IoT devices with decentralized identity (DID) in Q4 2019, including a trusted tracker (Pebble), home IP camera (Ucam), and IoT gateway (AvoBoard). What makes these “things” truly unique is not just that they are blockchain-enabled, but also enable full **end-to-end trust **, which we explain in the context of IoT devices below.
End-to-End Trust
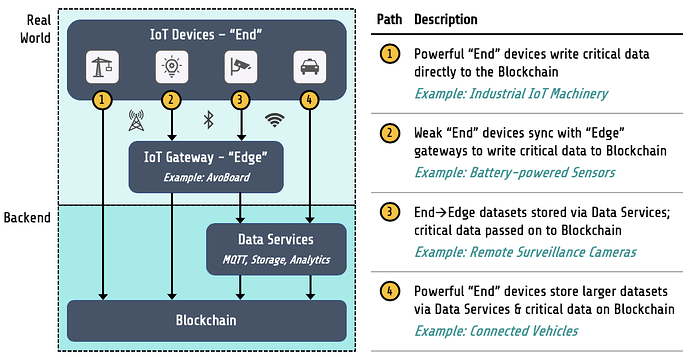
The IoT data life cycle involves multiple handoffs from IoT devices (“end”) to gateways (“edge”) to backend infrastructure (e.g., blockchain, Cloud), after which data is usable in applications (e.g., computing, data sharing, marketplaces). As illustrated below, there are multiple paths for IoT data from the real world to the backend to applications, depending on the specific IoT use case. Each specific path comprises a unique set of handoffs, all of which must be individually trusted to enable collective end-to-end trust.
On one end, we have the “physical” real world. This includes IoT devices and gateways, which pass data downstream via various wireless connectivity standards (e.g., WiFi, cellular, BLE). To ensure full trust, IoTeX leverages TEE-based secure hardware and in-house Decentralized Identity (DID) framework.
- Secure Hardware: TEE-based, tamper-proof devices, and gateways ensure integrity and confidentiality of data (note: IoTeX develops secure hardware in-house; Pebble Tracker & AvoBoard in Q4 2019)
- Decentralized Identity (DID): secure, self-sovereign identities are assigned to all “things” (people, devices, businesses) in the IoTeX Network, ensuring data senders/receivers are validated
On the other end, we have the “virtual” backend. IoTeX utilizes a hybrid Cloud/blockchain backend that is designed to protect data-at-rest while allowing data owners to authorize its use in trusted applications. With IoTeX, you own your data and how it is used in trusted computing, data marketplaces, and more.
- Trusted Computing: fine-grain controls for which OS, applications, and services may access your data, as well as privacy-preserving computations without any risk of leaking/exposing sensitive data
- IoT Data Marketplaces: end-to-end trust of data from trusted device to trusted backend enables buy/sell/trade of data without the need for a central intermediary; blockchain is the “fully trusted data broker”
Guaranteeing full end-to-end trust and privacy for data-in-transit, at-rest, and in applications is what truly differentiates IoTeX from all other blockchains and traditional solutions. Utilizing our advanced technology stack of blockchain, secure hardware, and data services, IoTeX will provide native, end-to-end trust for a variety of use cases and empower the new decentralized future. Welcome to the Internet of Trusted Things — we can’t wait to see what you will build with IoTeX!